How We Stopped Cybercriminals' Emails In Their Tracks
- Anthony
- September 14, 2018
- 04:56 PM
- No Comments
It's simple and affordable for all businesses.
This week, we’ve had several reminders of just how important cyber security is. Like any business, our email inboxes receive tons of spam every day, the majority of which goes straight to our junk email folders, but over the past few days we’ve seen a substantial increase in a type of attack that is unlikely to be stopped by basic email filtering: display name attacks.
These involve emails that appear to be from one person (a customer or staff member, for example), when they are in fact from another person (the criminal). In our case, most of these emails were pretending to be internal messages from one staff member to another, but there were some that used the names of customers.
If such emails get through your spam filter and reach a staff member, there are a few ways they can cause trouble.
Invoice fraud is a favourite among cyber criminals. This simply involves emailing someone, taking on the identity of someone like their boss or a supplier, and requesting an urgent payment. They’ll attach an invoice which will look legit, but in fact the bank details will be for an account of their choosing. In the past, businesses have lost several thousands of pounds to such scams.
 How much could your business afford to lose before it's too much to come back from?
How much could your business afford to lose before it's too much to come back from?
Also common is for scammers to attach documents like invoices, but instead of hoping their victim will transfer cash to them, they inject malware into their email attachment. When the recipient opens the file, the malicious code runs, and from there it can do all sorts of unhelpful things like:
- Installing a keylogger, a program that spies on your keyboard presses, to steal passwords and other sensitive information, which is then sent to the scammers.
- Launching a ransomware attack by encrypting files or even whole drives.
- Installing viruses, worms and other nasties, with the intention being to cause damage or data loss.
- Stealing your system’s computing resources, using it as part of a botnet or to mine cryptocurrency.
Cyber criminals can do a similar thing without attachments, by including links in their emails, which take users to malicious websites that install dangerous code or trick the victim into handing over important data.
Such threats are a growing problem for businesses, and it only takes one person within an organisation to trip up for huge financial losses to become a reality.
In our recent case, we sent several fraudulent emails, all requesting payment for an attached invoice. As you’d expect, these files were riddled with malware, but thankfully none of them made it to their intended targets – all real employees at TMB.
What stopped them? Microsoft’s Advanced Threat Protection (ATP), which can be added to Office 365 subscriptions. As these fraudulent emails came in, ATP scanned them, found the code and ran it in a ‘detonation chamber’ hosted by Microsoft in a remote server, far away from our business. When it tried to carry out the malicious activity it was designed to, ATP recognised it for what it was and stopped it being delivered.
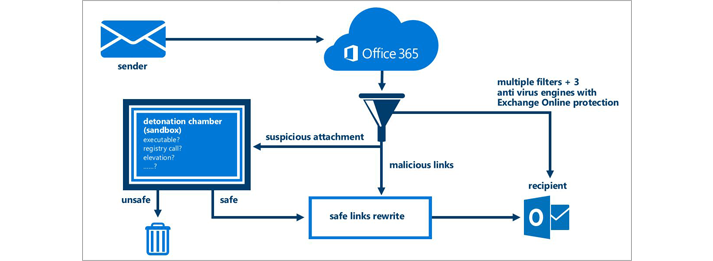 Microsoft's Advanced Threat Protection makes sure unsafe links don't catch you out.
Microsoft's Advanced Threat Protection makes sure unsafe links don't catch you out.
As this happened, our security admin received alerts from ATP informing him of these attacks. He was then able to inform the rest of the company, raising awareness and reducing the risks to the business.
Had ATP not been there, who knows what might have happened. Hopefully, because our staff all receive security awareness training, even if these emails got to where they were meant to go, our people would have had the ability to see they were fake.
But for organisations without adequate security measures or well-trained staff, the picture, sadly, looks much more uncertain.
You can read more of our cyber security blog posts here. If you're concerned about the state of your organisation's cyber security measures, please contact TMB to find out how we can help.

