How To Protect Your Business From Scam Email
- Anthony
- December 7, 2017
- 09:27 AM
- No Comments
Scam email is costing businesses millions of pounds every year, and everyone is a potential target. But there are ways to shield yourself from it and keep your business safe.
Although most of us accept spam email as an inevitable part of modern life, the scams that are often perpetrated through them can be extremely costly to the victims. But it’s not just individuals who need to be on the lookout for scam email: businesses are also a target – and, as you might imagine, a potentially lucrative one for scammers. In fact, last year, among the 2.9 million UK businesses that found themselves in the crosshairs of cyber criminals (at a total cost of £29.1 billion), phishing emails were by far the most prevalent.
And no business is immune to scam email. Indeed, the TMB team recently found itself targeted by one of these phishing attempts. We did, of course, already have ways to deal with it (more on that shortly), but it served as a good reminder to be vigilant against these kind of attacks. It also demonstrated a few techniques that criminals use, and which all businesses should be aware of.
https://youtu.be/BssEr-JK4Gg
Spear Phishing
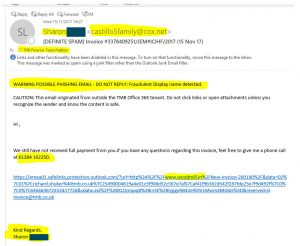 The scam email we received (click to see full-size image)
The scam email we received (click to see full-size image)
The email in question was sent to the TMB finance team, and read as follows:
“Hi,
“We have still not received full payment from you. If you have any questions regarding this invoice, feel free to give me a phone call at 01384 [rest of number removed]”
This was followed by a long web link (see image), stretching over three lines. Then, at the bottom:
“Kind regards,
Sharon Smith [name changed to protect the innocent]”
A few things were going on here. Firstly, TMB does employ someone called Sharon Smith, and not only was her name at the bottom of the email, it was also in the display name at the top.
Secondly, the actual link sent to us was www.woodmill.in. Extra text in the link was added by a Microsoft feature called ATP safe links, part of Office 365 Advanced Threat Protection. This detects any web links in your emails, and alters them. If you click on one of these altered links, then instead of being taken directly to the website in question, it's checked by Microsoft, and if anything untoward is going on, you’ll be safeguarded against it.
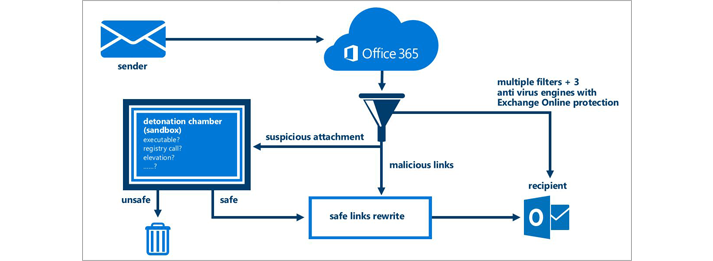 Microsoft's Advanced Threat Protection makes sure unsafe links don't catch you out.
Microsoft's Advanced Threat Protection makes sure unsafe links don't catch you out.
In our case, the link presumably would have taken the finance team to a website where they could pay this apparent invoice. This would either send money to a scammer’s bank account or simply steal the data that was inputted – perhaps both.
The fact that a real TMB employee’s name was used in the email is a significant point too. Targeting a company in this kind of specific way is called spear-phishing. Regular phishing emails are more generic attempts to steal information, whereas spear-phishing requires a certain degree of research beforehand - but it’s research that often pays off for criminals.
Display Name Spoofing
Not only was the name at the bottom Sharon Smith, the display name (the name at the top of the email) was as well. This is known as display name spoofing – and it’s been linked with an astounding 91% of phishing emails to corporate inboxes.
It’s not a sophisticated technique at all, and you’ll notice the email address was completely wrong. Instead of showing Sharon’s name or the company’s domain name, it read ‘castillo5family@cox.net’.
Why would criminals use such a flimsy technique to hide their ruse?
One reason is simply because it’s easy. But they’re also relying on their victims being so swamped with emails that they don’t notice the suspicious email address. Also, many people check their email on their smartphones, and some of the most popular email apps on mobile phones only show the display name and not the email address.
Funnily enough, scammers can also spoof the email address too, if they want. In our case, it would have read something like sharon.smith@tmb.co.uk, but it would actually come from an entirely different email address. This is sometimes known as direct spoofing.
Naturally, this is a more effective phishing technique, but it's not one you'll actually see that often. Email and software vendors have made great strides in combatting it, using something called SPF (Sender Policy Framework) records. These check email addresses against a record of IP addresses (unique numbers that reveal a person’s location), to make sure emails are coming from who they say they’re coming from. If the information doesn't match up, the email never gets delivered to the scammer's intended target.
But SPF records have proven so effective that many criminals don’t even bother with direct spoofing any more. With simple display name spoofs, they actually have more chance of their phishing emails getting past businesses’ firewalls.
Fighting Scam Email
How do you protect your business from these fraudulent emails? First and foremost, you need to know how to identify phishing attempts. That way, if anything gets through your spam filters, you’ll still be able to recognise it as spam. In this case, not only did we notice that the email address of the apparent sender was wrong, we also saw the phone number was a fake. The area code was for Dudley – nowhere near any of the TMB offices. Furthermore, the link included a completely unrelated web address: www.woodmill.in.
Of course, as you can see from the screenshot, our Outlook email server also detected the fraudulent display name, and it inserted a prominent message at the top to warn the user. This is not a feature of Outlook by default, but rather something the TMB engineers set up. What it does, essentially, is run a check when it detects the name of one our team. If the email doesn’t match the one on record for that person, it’s flagged as spam, and a notification is sent to our security people.
Combined with SPF records, cyber security software and team training, we've built an effective barrier against phishing emails. No solution is ever going to be 100% perfect, of course, but they can dramatically reduce the risk of businesses falling victim to these scams.
Final Thoughts
Burying your head in the sand is not an option, especially because it's not just time and money at risk. If cyber criminals manage to get hold of personal information through a scam email, you might also find yourself in breach of the law.
Bearing that in mind, robust email security is not a luxury but an absolute necessity. There might be some short-term costs involved, depending on the current state of your IT solutions, but ultimately the cost of doing nothing could be much greater.


